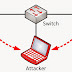
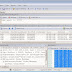
Thursday, 11 February 2021
Friday, 29 January 2021
Thursday, 28 January 2021
Monday, 5 August 2019
Sunday, 31 March 2019
Saturday, 23 February 2019
Monday, 22 August 2016
Thursday, 21 April 2016
Monday, 21 March 2016
Friday, 23 October 2015
Monday, 13 April 2015
Monday, 6 April 2015
Friday, 3 April 2015
Tuesday, 24 March 2015
Sunday, 22 March 2015
Saturday, 7 March 2015
Thursday, 5 March 2015
Sunday, 1 March 2015
Monday, 9 February 2015
Thursday, 29 January 2015
Monday, 15 December 2014

















.jpg)