 Echo Mirage 3.1 :: Tools
Echo Mirage 3.1 :: Tools
Echo Mirage is a generic network proxy. It uses DLL injection and function hooking techniques to redirect network related function call...
 Echo Mirage 3.1 :: Tools
Echo Mirage 3.1 :: Tools
Echo Mirage is a generic network proxy. It uses DLL injection and function hooking techniques to redirect network related function call...
 Orbot (Tor for Android Devices) :: Tools
Orbot (Tor for Android Devices) :: Tools
Orbot is a free proxy app that empowers other apps to use the internet more securely . Orbot uses Tor to encrypt your Internet traff...
.png) Crypto Implementations Analysis Toolkit :: Framework
Crypto Implementations Analysis Toolkit :: Framework
The Cryptographic Implementations Analysis Toolkit (CIAT) is compendium of command line and graphical tools whose aim is to help in th...
 DriveCrypt (Disk Encryption) :: Tools
DriveCrypt (Disk Encryption) :: Tools
DRIVECRYPT securely and easily protects all proprietary data on notebooks and desktop computers 100% of the time without users having...
 Harden SSL/TLS (Hardening the SSL/TLS Settings) :: Tools
Harden SSL/TLS (Hardening the SSL/TLS Settings) :: Tools
Harden SSL/TLS allows hardening the SSL/TLS settings of Windows 2000,2003,2008,2008R2, XP,Vista,7. It allows locally and remotely set...
 Fern WiFi Cracker (Wireless Security Auditing) :: Tools
Fern WiFi Cracker (Wireless Security Auditing) :: Tools
Fern Wifi Cracker is a Wireless security auditing and attack software program written using the Python Programming Language and the P...
 Maligno (Penetration Testing) :: Tools
Maligno (Penetration Testing) :: Tools
Maligno is an open source penetration testing tool written in python, that serves Metasploit payloads. It generates shellcode with ms...
 Advanced Encryption Package :: Tools
Advanced Encryption Package :: Tools
Advanced Encryption Package is a File encryption , Secure File Transfer, Batch File Encryption and Encrypted Backups. Advanced Encryptio...
 SSLsplit (MITM Attack against SSL/TLS) :: Tools
SSLsplit (MITM Attack against SSL/TLS) :: Tools
SSLsplit is a tool for man-in-the-middle attacks against SSL/TLS encrypted network connections. Connections are transparently interc...
 Hash Generator :: Tools
Hash Generator :: Tools
Hash Generator is the FREE universal hash generator tool which automates the generation of 14 different type of hashes or checksums. ...
 Online WPA Cracker :: Tools
Online WPA Cracker :: Tools
Online WPA Cracker is a online tool that crack you WPA encryption but you have to pay for it. An online WPA cracking tool which auto...
 Beast-Check (SSL/TLS BEAST Vulnerability Check) :: Tools
Beast-Check (SSL/TLS BEAST Vulnerability Check) :: Tools
Beast-Chec k is a small perl script that checks a target server whether it is prone to BEAST vulnerability via target preferred ciphe...
 TOR :: Tools
TOR :: Tools
Tor is a network of virtual tunnels designed to improve privacy and security on the Internet by routing your requests through a serie...
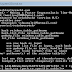 RainbowCrack (Hash Cracker) :: Tools
RainbowCrack (Hash Cracker) :: Tools
The RainbowCrack tool is a hash cracker that makes use of a large-scale time-memory trade-off. A traditional brute force cracker tri...
 TrueCrypt (Disk Encryption System) :: Tools
TrueCrypt (Disk Encryption System) :: Tools
TrueCrypt is an powerful open source disk encryption system for operating system Windows, Mac, and Linux systems. Users can encrypt e...